Information Security Policy¶
Overview¶
CloudAEye delivers multi-tenant SaaS services. This document describes our information security policy and frequently asked questions (FAQ).
We focus on topics such as "principle of least privilege and enforce separation of duties with appropriate authorization for each interaction", "apply security at all layers", "protect data in transit and at rest", "automate security best practices", etc. to deliver secure and reliable multi-tenant SaaS services.
Frequently Asked Questions (FAQ)¶
Data Flows¶
Describe in detail how customer data flows to CloudAEye SaaS?¶
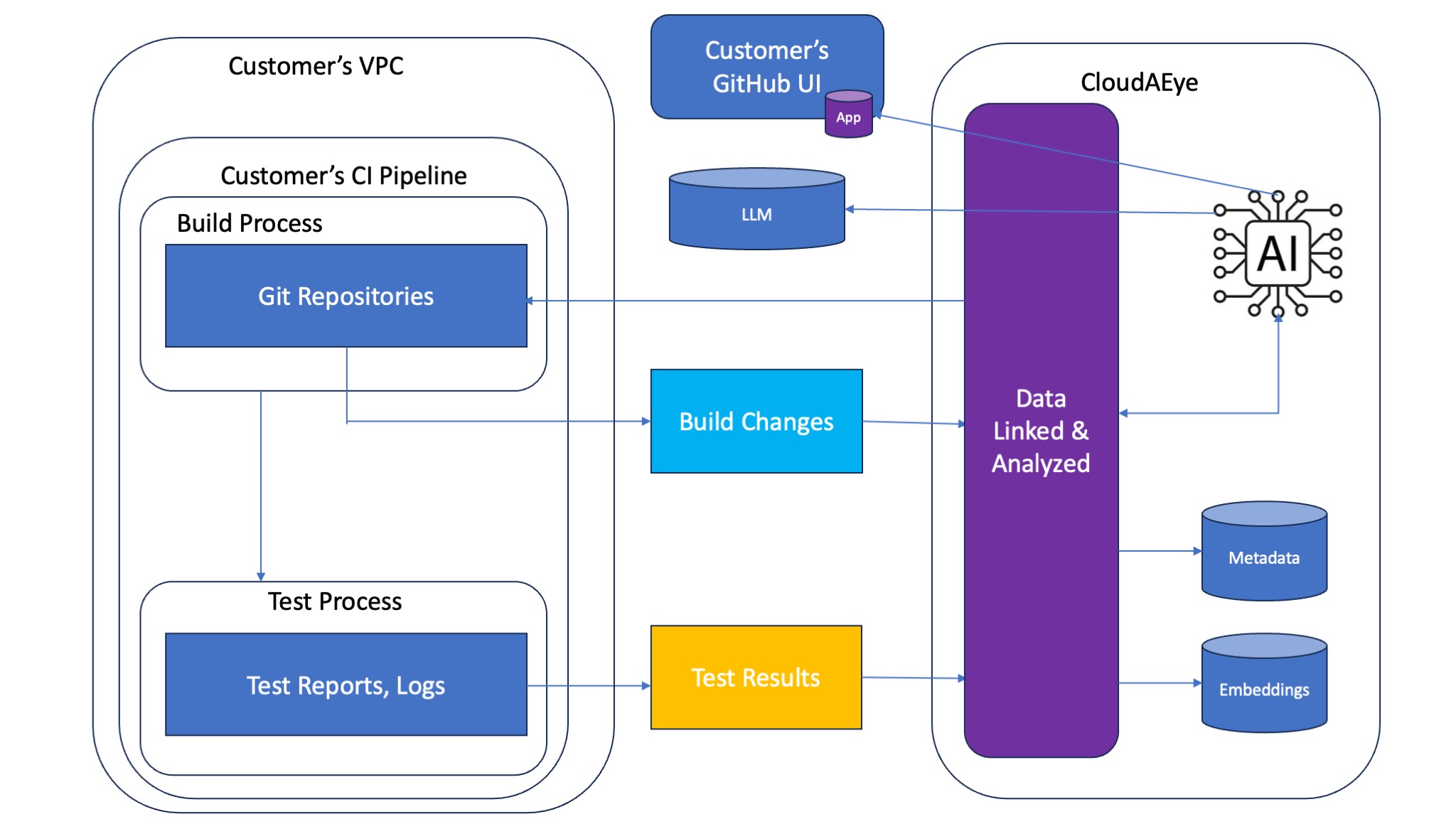
CloudAEye is a multi-tenant SaaS. No customer data is stored in CloudAAEye. Only metadata and embeddings are stored. These can also be stored in customer's VPC. Please refer to Trust Center to learn more about deployment options.
Data is accessed from a customer's GitHub or Bitbucket site by CloudAEye during a code review analysis. For test failure analysis, we access test logs in CI.
We ensure that customer data is secure by encrypting it both in transit and at rest. For data in transit, we use HTTPS and TLS (Transport Layer Security), as well as the AWS Signature Version 4 signing process.
Certifications¶
Does your company have any attestation reports or security certifications (e.g. PCI, SOC, ISO, FedRAMP, HITRUST)?¶
We inherit the certifications that our cloud provider (AWS) maintains. These are SOC2 Type 2, ISO27001, and ISO27017.
Access and Identity Management¶
Does your Information Security policy contain an Access and Identity Management, or equivalent, policy?¶
Yes. We manage privilege using centralized identity and access management. All human identities and access are managed using role-based access control (RBAC) policies. Our overall architecture enables access control at multiple levels. For machine identities, we control access using AWS access keys. This way, we can ensure that customer data is always secure and protected.
Permissions Management¶
Is access to personal information limited only to those individuals that need access to the information to perform the services?¶
Yes. Access controls are specifically granted only to individuals whose job function requires it. We grant least privilege access that identities require to perform specific actions. We revoke permissions when user no longer need them to minimize risks.
Patch Management¶
Does your company have a patch management process?¶
We use infrastructure-as-code principals. We deploy using CI/CD to reduce the number of security misconfigurations into a production environment. We use canary CD to deliver our patches with zero-downtime.
Incident Response¶
Does your company have an Incident Response Plan?¶
Yes. We can furnish details upon request. In the event of a major incident, the Incident Manager prioritizes it over any other activity CloudAEye is undertaking.
Change Management Process¶
Has your company implemented a formal change management process for all product changes that impact your customers?¶
Yes. We can furnish details upon request. We take a structured approach to managing change and evaluate all options when dealing with changes that may impact customers and partners.
Business Continuity Plan¶
Does your company have a Business Continuity Plan (BCP)?¶
Yes. We can furnish details upon request.
Disaster Recovery Plan¶
Does your company have a Disaster Recovery Plan (DRP)?¶
Yes. We can furnish details upon request.
Risk and Vulnerability Management¶
Does your company have a Risk Management Program?¶
Yes. We can furnish details upon request.
Application Security and Development¶
Does your company use a staging or pre-production environment to build, test, and validate before promoting to production?¶
Yes. We isolate our environments such as dev, staging, and prod for each service. Each environment may use a different AWS account. This isolation establishes guardrails for security, billing, and access.
Is your company's production code covered by automated testing?¶
Yes.